Table of contents
Recap
Last week we skimmed through some salient features of public Blockchain & compared it with Ethereum. We also explained the need for cryptocurrency in a Blockchain & the differing objectives of Bitcoin & Ether in line with their respective platforms.
We then discussed scarcity of resources (memory, processing power, storage space) in computers & extrapolated their impact in a Blockchain. From there we explored how GAS fees & ether is used to pay for & track resources provided by the Ethereum platform.
Today we will explain how a user can interact with Ethereum in the first place.
Wallets
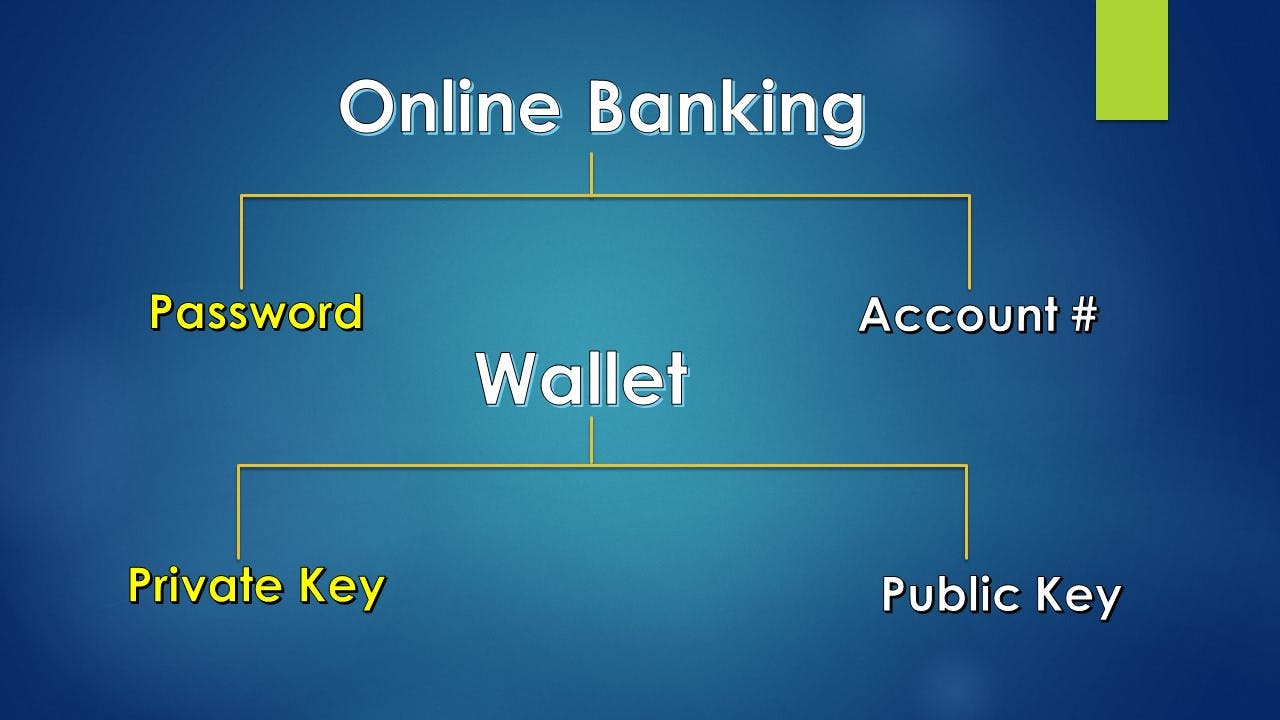
We discussed wallets in Week 19 in the context of Bitcoin payments. Wallets can be considered like browsers. We can access blockchains only through wallets like we access the world wide web or internet through browsers. To recap, a wallet :
a. Controls access to a user's cryptocurrency
b. Manages keys & addresses
c. Signs transactions &
d. Tracks balances of cryptocurrency
External Owned Accounts (EoAs)
Before we deep dive into wallets, let us take a step back on who or what initiates transactions in Ethereum. A transaction can be initiated by
A user who holds a wallet and provides the necessary instructions to carry out a transaction or
A contract when a condition (or conditions) to initiate a transaction is satisfied
The type of account where a transaction is initiated by a user using a wallet (users can initiate transactions only through wallets) is called Externally Owned Accounts. We know that a wallet contains public & private key pairs which is used in its interaction with the Blockchain. So, EOAs are accounts which have a public & private key.
Let us do a refresher on keys (From Week 19) :
Private Key - key which is used by the initiator of a transaction to encrypt the contents of the transaction.
Public Key - key (of the initiator) which is used by the recipient to decrypt or decode the encrypted transaction.
Thus only a person who has access to the sender's public key can decrypt a transaction encrypted by the sender's private key.
The concept of using a paired public & private key system is called ASYMMETRIC CRYPTOGRAPHY.
Asymmetric cryptography enables users who do not know each other to exchange encrypted information.
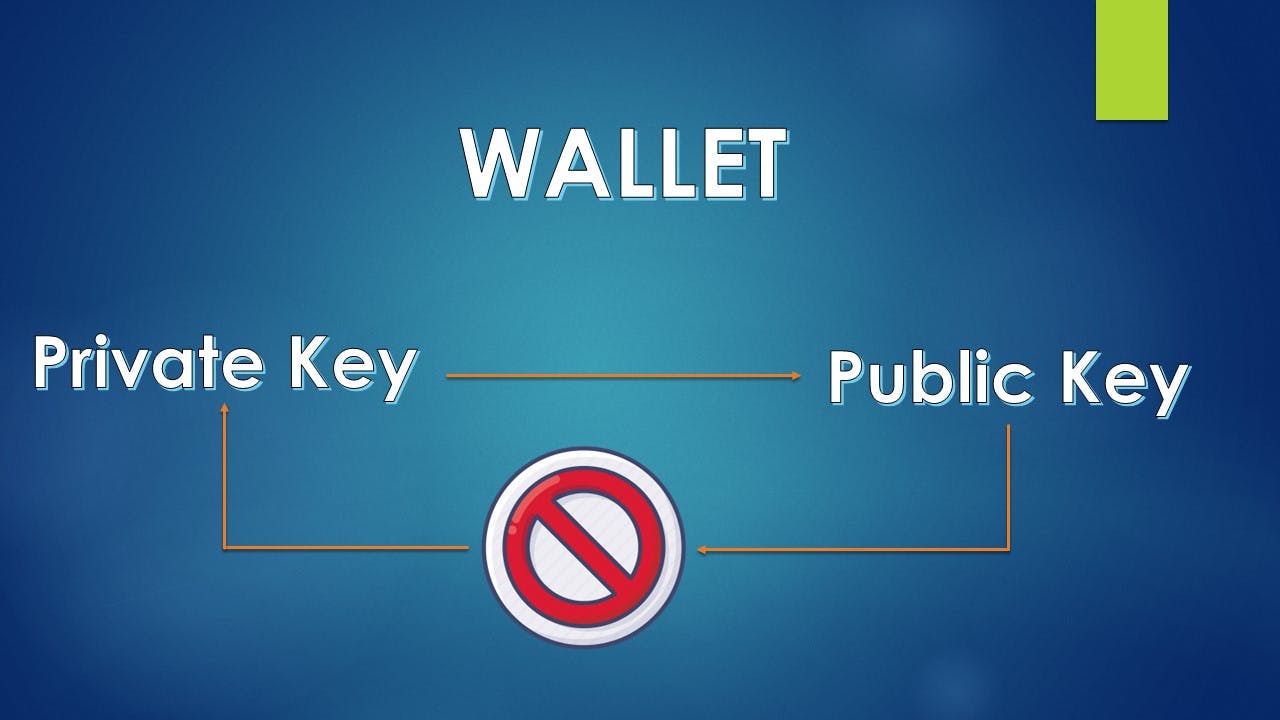
A public key is made available to all. It is like a bank account number, which can be provided to anyone.
The private key, which remains secret, acts like a password to the same bank account.
- The public key is derived from the private key, but cannot be reverse engineered back to arrive at the private key.
- From the private & public keys is derived what is known as Addresses which are unique identifiers (like beneficiary details in traditional banking).
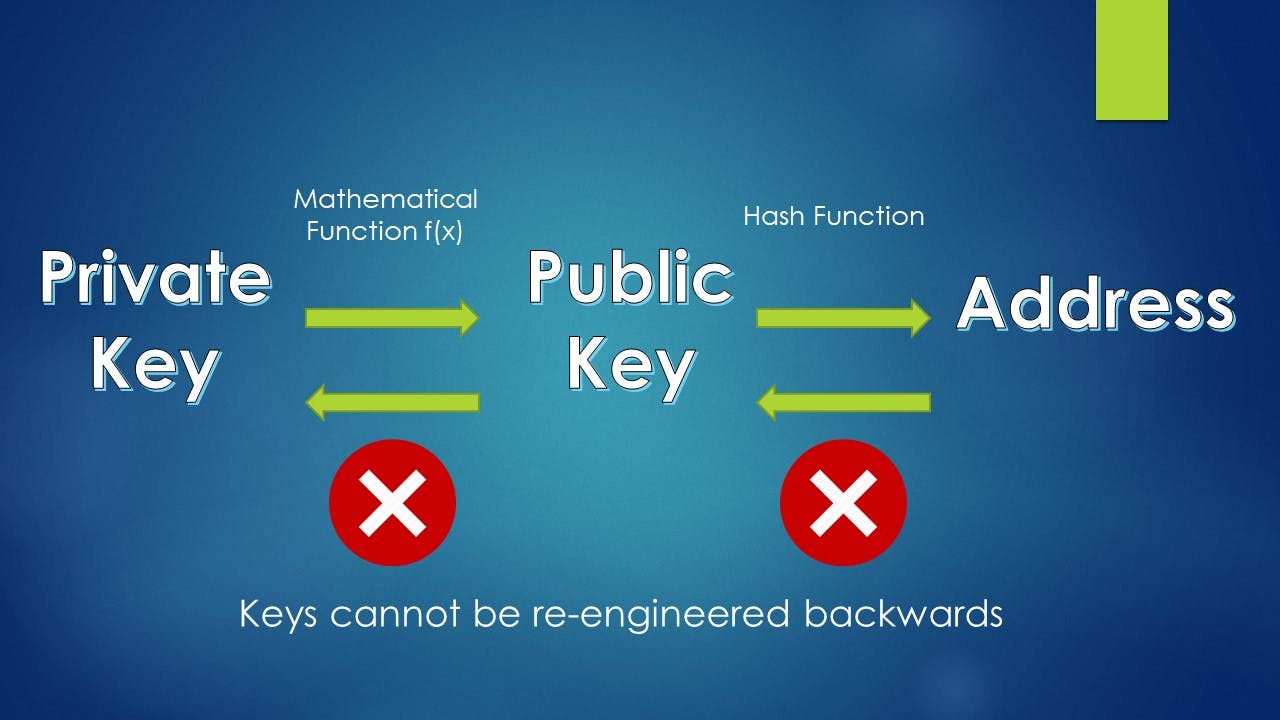
Why do we need all these keys & cryptography? The answer is straightforward - To control access to Ether in a secured manner.
Wallets are like key-chains which are "linked" to the Ether in the Ethereum Blockchain. This "linkage" implies ownership which is proved through keys.
Thus, ownership of Ether is established through private keys held in wallets using digital signatures & addresses. Users sign transactions with keys from their wallets.

Photo by cottonbro:
I mentioned in one of my earlier blogs that a digital signature is generated on a transaction which is a combination of the private key & the transaction imprint. When a transaction is initiated in order to transfer funds, it has to be signed with a digital signature created with the private key corresponding to the the sender's address.
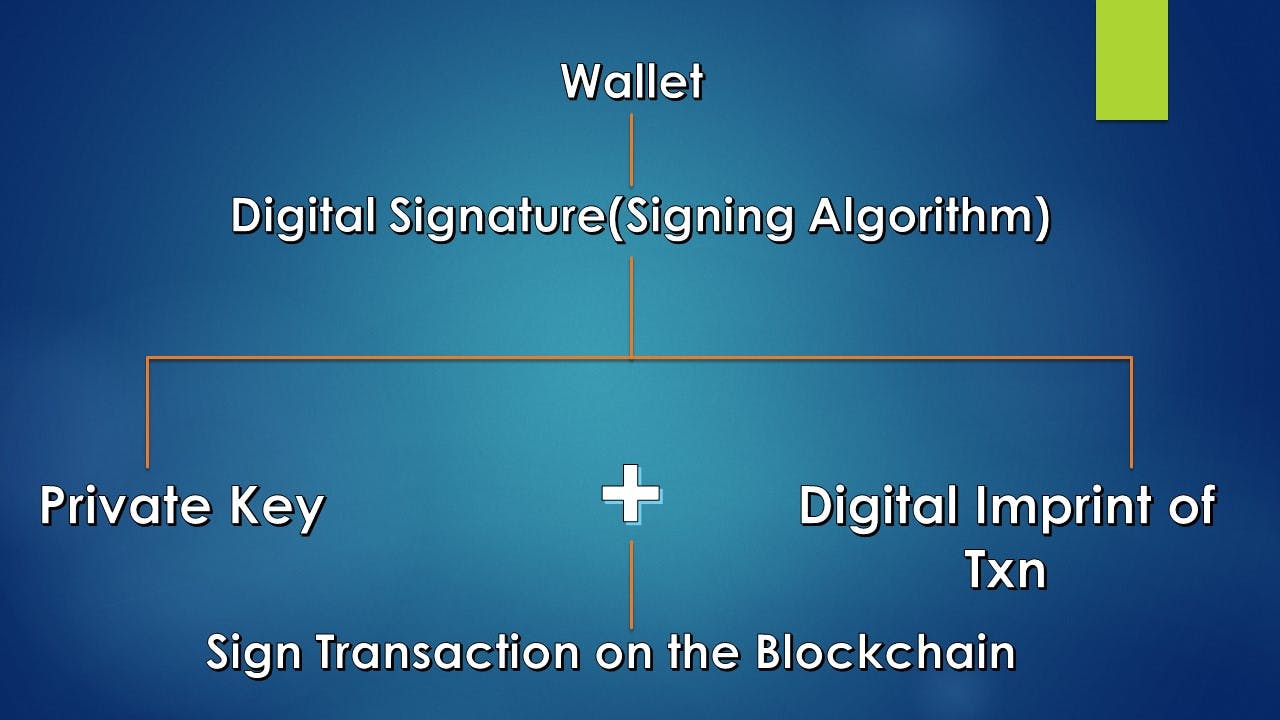
Access & control of Ether is achieved through digital signatures. Anyone with access to a private key has control of the corresponding account & any Ether it holds. (Hence, it is important to keep your private keys safe using best practices in key security & management)
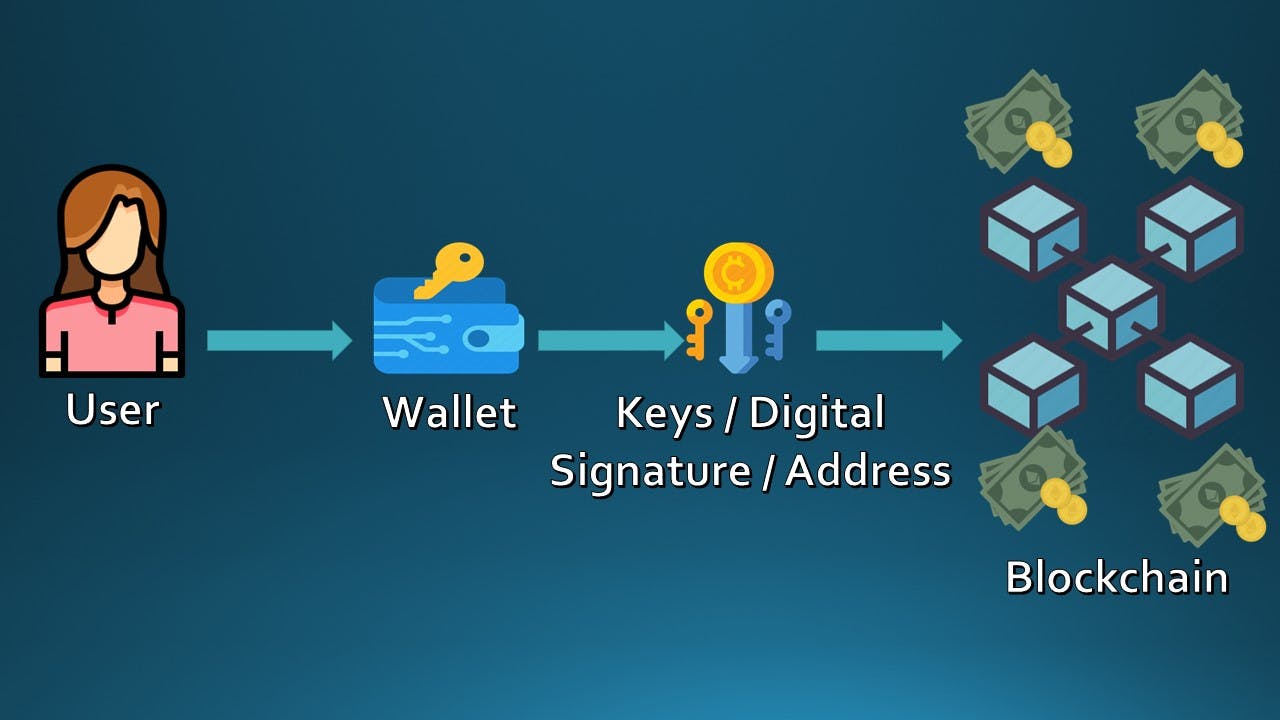
All the processes underlying key generation, control & digital signatures are carried out in a wallet. Most of the time, users are not aware of the underlying mechanisms around key management & storage in their wallets.
Thus,
Wallets are software applications that serve as the primary user interface to Ethereum.
Wallets control access to the user's cryptocurrency, manage keys & addresses, creates & signs transactions & tracks balances of cryptocurrency corresponding to that address.
Keeping the above concepts in mind, let us dig a little deeper into wallets