Table of contents
Recap
Last week we introduced blockchain classifications based on permission. These are:
- Public Blockchain
- Consortium Blockchain &
- Private Blockchain
Before we go into the pros and cons of one over the other, let us explore an important aspect of blockchain vulnerability.
Blockchain Hacks
In this age of digital transformation, software selection assumes a central part in the whole process. In addition to support, upgrades and customization, another important aspect when selecting a software is security. However, this consideration may differ for a blockchain.
Why?
A software is normally deployed in a centralized server along with synced back ups while a blockchain client is downloaded in laptops or computers of nodes which are scattered across the globe.
Currently, one of the major reasons hacks are initiated is to access identities, usernames and passwords with the underlying data and sell it in the dark web for monetary gain and of course,
To steal the victim's cash from their bank accounts. Normally, these are carried out through phishing, social engineering etc.
In centralized organizations like banks or Financial Institutions, data is held internally in organizational servers and safeguarded with adequate security measures to be in compliance with rules & regulations related to data privacy & related regulations. But in a public blockchain, data is visible for all to see. The transactions can be seen by anyone. Nodes can join and leave at any time, validate transactions & mine blocks without any restrictions. So, why should someone steal data from a blockchain which are already visible for the world to see.
It is not all about the data. It is about the the underlying cryptocurrencies or to reverse a spent transaction back to the spender so it looks like he or she has not spent the amount.
Well, wait. Isn't a blockchain protected by built in security features like cryptography, hashes etc which makes it "unhackable"?
Unfortunately, blockchains are not immune to attack and there are numerous examples of such hacks. Any technology has weak points & attack vectors through which hacks are initiated. The attacks can come from outside or initiated by an insider. The methodology used is common like phishing, social engineering, finding vulnerabilities in code etc.
Let us focus on hacks specific to blockchain. There are two types of blockchain specific hacks :
- Sybil Attack
- 51% or Majority Attack
Sybil Attack
Let us consider a blockchain with 11 nodes as below :
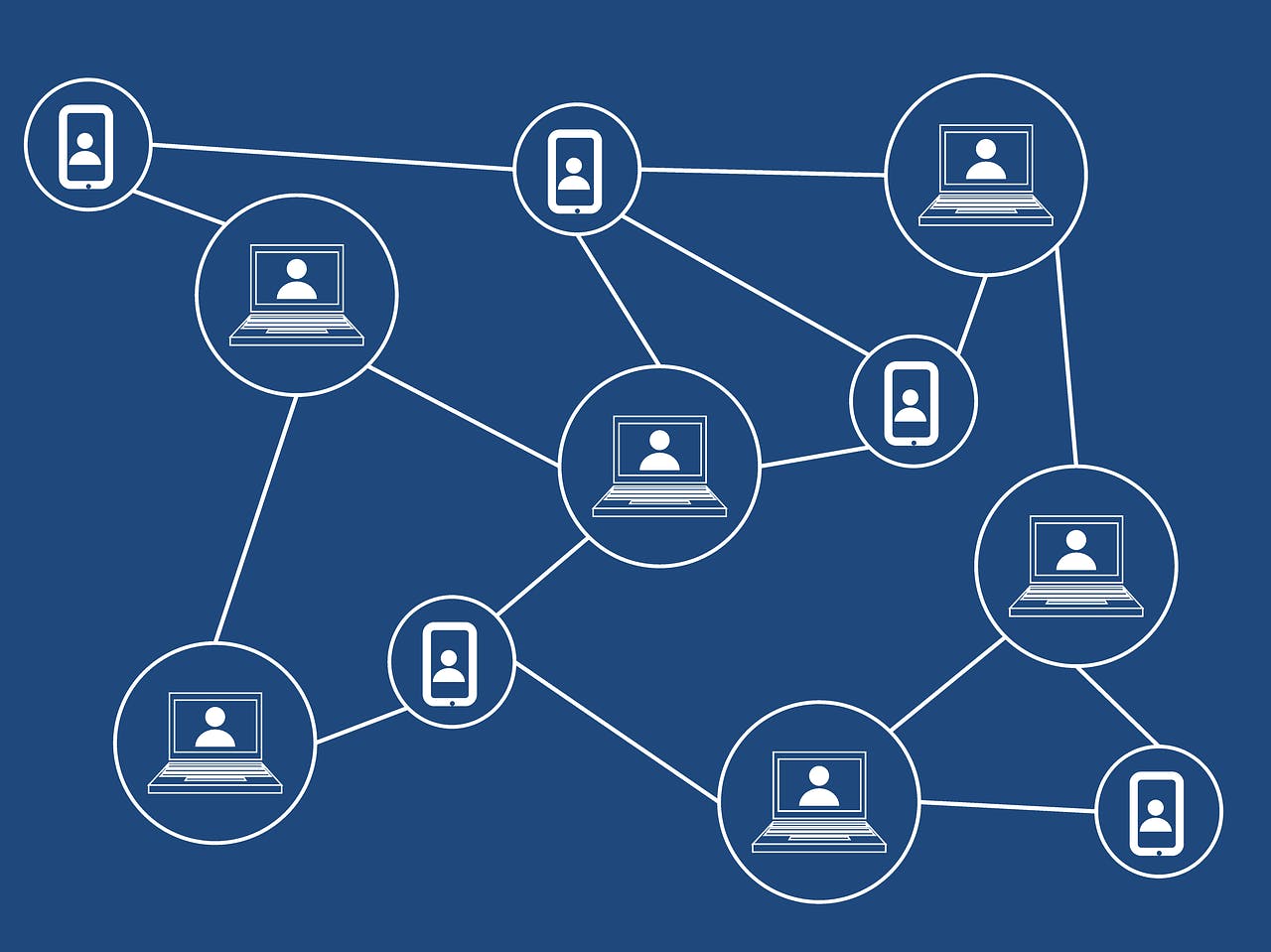
Assume that 6 out of 11 nodes are operated by the same entity or person but with different identities. This entity or person will have undue influence over the blockchain network and disrupt the functioning of the network. It is the same as someone creating multiple Facebook or Twitter accounts.
These dishonest nodes can prevent validation of transactions & blocks. They can refuse to receive, transmit or validate blocks and also reverse transactions leading to double spending.
So, how are sybil attacks prevented?
We know that blockchains use consensus algorithms to agree on creation, validation & authentication of transactions & blocks. We saw how "Proof of Work" algorithm requires tremendous processing power to mine a block. So, to do a sybil attack, all of these dishonest nodes need to have a majority combined hash power to overcome the honest nodes' hash power.
Thus consensus algorithms do not prevent sybil attacks but makes it very difficult & costly to execute one.
As per wikipedia
A Sybil Attack is a type of attack on a computer network service in which an attacker subverts the service's reputation system by creating a large number of pseudonymous identities and uses them to gain a disproportionately large influence.
51% Attack or Majority Attack
Let us go to another blockchain :
Image by Maicon Fonseca Zanco from Pixabay
There are a lot of nodes connected to each other. We all know that miner nodes are the ones keeping the blockchain network functioning in line with the underlying consensus protocols. Miner nodes add blocks by solving proof of work algorithms. This is done by using their CPU power or processing power (also called Hash Power).
Once a block is mined, it is broadcast to all the nodes who then validate it and add it to the last block in the blockchain or reject it if found invalid.
Now, assume a scenario where a miner includes one or more invalid transactions like reversing spends putting the amount back to the spender (called double spending ). In a normal scenario, this would be rejected by the other nodes.
However, to ensure this fraudulent transactions are accepted in a block and validated, the miner node has to control a majority of the processing power of the entire blockchain network as the respective dishonest nodes will validate this invalid transaction.
Thus, this type of attack is called a 51% attack because whoever controls more than 50% of the hash power can control the entire network and validate fraudulent or wrong transactions benefiting them.
Satoshi Nakamoto in his white paper also referred to the above scenarios as below :
The proof-of-work also solves the problem of determining representation in majority decision making. If the majority were based on one IP address one vote, it could be subverted by anyone able to allocate many IPs.
Proof-of-Work is essentially one CPU, one vote. The majority decision is represented by the longest chain, which has the greatest proof-of-work effort invested in it.
If a majority of CPU power is controlled by honest nodes, the honest chain will grow the fastest & outpace any competing chains.
So, the bigger the network (more number of nodes), more processing power or Hash Rate is required to subvert the network which makes it costly to do so.